candle_86 wrote:
current situation is this, I rent a room in someones house to save money, as im single and simply prefer roommates since my last apartment got broken into in broad daylight, and a 65in TV, my desktop, my Xbox, my PS3, my Genesis, n64 and Microwave walked out the door, on a Saturday at 11am. None of the neighbors noticed they claim. So I simply do not wish to live by myself for security reasons. My landlord pays for the internet connection, and thus it is wifi, i can pay for a mobile hotspot, but its expensive and has limited bandwith, as for a wired connection, that wouldn't solve the problem of access to my other computers, my main windows 8 box hasn't been touched by him, he likes playing around inside my windows me and 2000 boxes, he hasn't harmed them, but he has moved things around, and even replaced my wallpaper. I'd block his connection but he uses the DHCP so id have to block all address besides 192.168.137.1-5 as well as 192.168.0.1 which is the router and when i tried that it didn't work so well.
With a separate connection you'd want a router, which would eliminate the connectivity problems for other machines (it would take the 'net in, and kick out a LAN; just like landlord's router is doing right now). It would also be separated from this guy. I wouldn't do a mobile hotspot though. If you went with a stand-alone router, like alexanrs suggested, it'd do effectively the same thing, but connect to the landlord's network as another "hop" before going out to the Internet. Currently that's what you're trying to have the Win8 box (Kirk) do with ICS, and it may simply be a matter of better configuring the firewall rules there to get what you want.
Question on your current configuration, however:
You have the WiFi connection hooked up to the landlord's network, and then you're using what to generate the output for your personal network? ICS? Or did you bridge the connections?
It should be setup via ICS, and ideally you selected "Public" for the landlord's network, and "Private" for your internal ring of machines. In principle this should secure your "internal network" of machines (e.g. Spock, McCoy, etc) via the ICS Firewall on your gateway machine (Kirk). I'd also kill UPnP (or restrict it; if you need it for some functionality on the landlord's network).
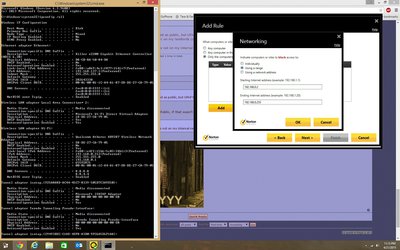
Blocking him (and anyone else on the landlord's LAN) via the firewall shouldn't be too hard either. Firstly, there's no reason to block 192.168.137.x addresses because that's the "internal ring" (e.g. Spock to Kirk - he isn't connected as a peer to Spock, he's connected as a peer to Kirk, so blocking Spock's peers is irrelevant), but you could block (from Kirk) everything except the gateway and DHCP server (they may have separate addresses - run tracert and ipconfig and figure out exactly where things are going). So for example say the gateway is 192.168.0.1, and the DHCP server is at 192.168.1.1, block everything else from 192.168.0.2 -> 192.168.0.255, and 192.168.1.2 -> 192.168.1.255, all ports (0-65535), inbound/outbound, all the time. It should absolutely kill connectivity to anything on the landlord's network beyond the gateway. You would want to set this as a rule for Public Networks, and then configure the WiFi adapter as being on a Public Network.
I would also create another outbound rule that blocks ports 139 and 445 while you're in there, to protect against SMB Redirect attacks (http://www.bit-tech.net/news/bits/2015/04/14/ … direct-to-smb/1 for more); if you lock those internally (e.g. you create a firewall rule on Spock) it will cause connectivity problems with local services (e.g. if McCoy is acting as a local file-server, Spock will have connectivity issues there; blocking it at the network gateway (e.g. Kirk) will allow internal features to work but still provide security from external threats).
Finally, remember if you take Kirk somewhere else and plug it into another network that you have this rule, because it will probably mess with connectivity in other environments. For example if you drag it over to a friend's house for a LAN party and want to hook up to their home network, you would need to disable this rule (or select that connection as a Private Network). 😊
As a side note: I enjoy using the Star Trek character names for this discussion. 😀