Reply 40 of 42, by clueless1
- Rank
- l33t
wrote:wrote:wrote:No one's brute forcing passwords though.
If that's true, then why are there so many brute force tools?
I should have specified, no one brute forces passwords to online accounts.
Even for offline passwords, brute forcing is a last resort. Who doesn't try "Password" before they try "xJ1%^ao2I,"? It only makes sense if you know the password is randomly generated and most people don't do that.
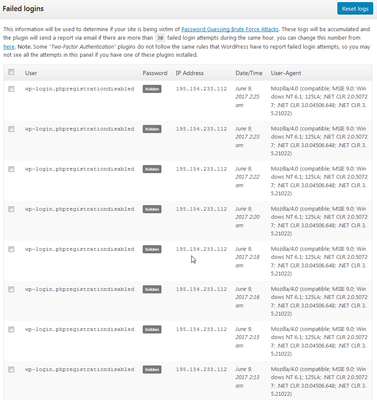
26 attempts in a 58 minute period from same IP and user agent. Wouldn't that be considered a brute force attack on an online account?
The more I learn, the more I realize how much I don't know.
OPL3 FM vs. Roland MT-32 vs. General MIDI DOS Game Comparison
Let's benchmark our systems with cache disabled
DOS PCI Graphics Card Benchmarks