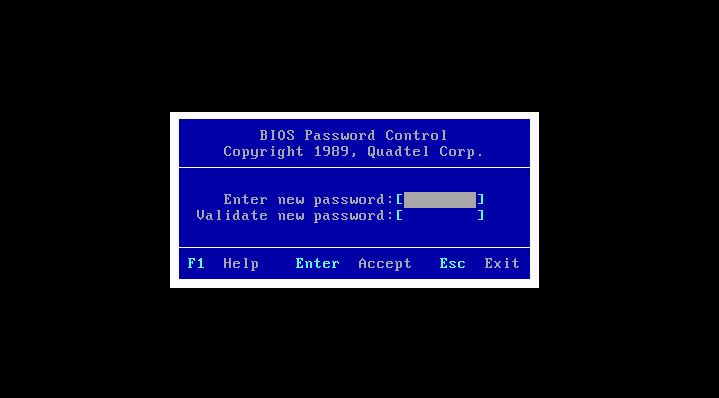
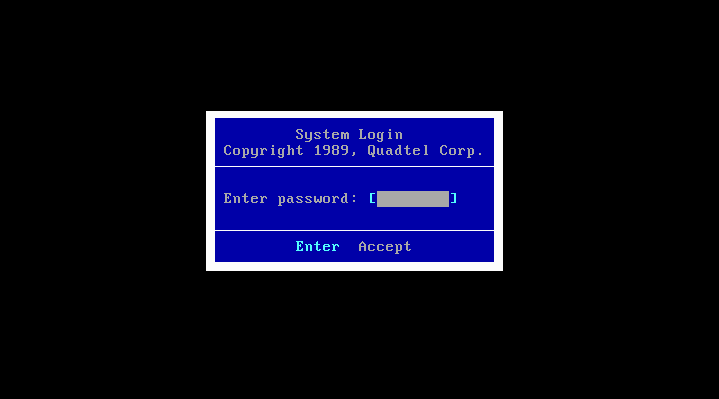
Sorry, I guess I should have been more detailed about this. 😅
I meant that it was a common pratice back then to protect a machine via the BIOS.
On boot-up the computer asked for a password, before booting the OS was possible.
Older BIOSes allowed the password to be set for either "SETUP" or "SYSTEM", if I'm not mistaken.
Im talking about 286/386 era BIOSes found on the more professional PCs.
Older versions of Phoenix and AMI BIOS, for example.
I think this feature was slowly phased out beginning with the 486 era.
Another idea was to block the keyboard by a key lock.
Without the lock in the right position the keyboard was non-functional (but was on).
Depending on the type of the machine, the keyboard could be locked and un-locked while the machine was running.
That's why some PC/XT mainboards do have a pair of "lock" pins.
With the advent of GUI driven OSes like Win95 this kind of protection also wanished
(on Win 3.1 you had to type "WIN" at least, so it was still useful to protect the keyboard.
Not all PCs had the WIN command in the autoexec.bat)
Some PCs also had another key lock for the power supply..
But back to the BIOS thingy..
The second picture shows the BIOS asking for a password on boot-up, unlike modern BIOSes,
which do often only ask for this if you're entering the setup utilitys.
"Time, it seems, doesn't flow. For some it's fast, for some it's slow.
In what to one race is no time at all, another race can rise and fall..." - The Minstrel
//My video channel//