First post, by ajacocks
- Rank
- Member
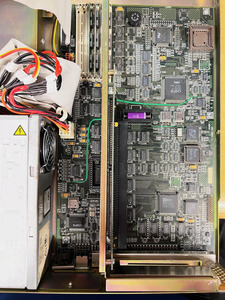
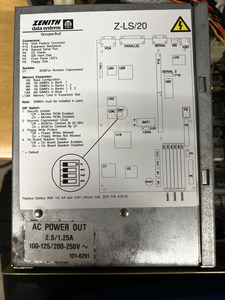
I just got a rather interesting low-profile 386SX/20 desktop from Zenith called the Z-LS/20. It’s a slim chassis with only a single 3.5” floppy drive, mounted facing right, rather like a SPARCstation 1, 1+, 2, or 10. When I received it, there was significant corrosion on the mounting tabs for the power supply, which turned out to be from long-remaining electrolyte from some leaked capacitors. I cleaned that up, scrubbed the PCB, and replaced the caps, and miracle-of-miracles, it actually worked.
The machine’s onboard VGA creates a sync signal, but I get nothing onscreen, so that needs to be troubleshot. However, with an accessory video card, I can see that the machine powers up and posts, and wants to have its CMOS options set. There is a BIOS password preventing that, though.
Normally, I’d use one of the DOS-based BIOS hacking tools to get the password, but I can’t set a boot device, and there is no option to skip the password. I also can’t find a reset jumper or set of pads, on the motherboard. It’s also interesting to me that there is a password at all, as the CMOS battery was 100% dead, when I received it. I assume that it must be a manufacturer-supplied default password.
I have already tried all of the passwords that I found on the various known BIOS password lists that I have found.
Any advice would be much appreciated.
Thanks!
- Alex