First post, by Exploit
I am trying to improve my x86-16 assembler skills and found this nice insight debugger on the FreeDOS 1.3 CD-ROM.
https://www.bttr-software.de/products/insight/
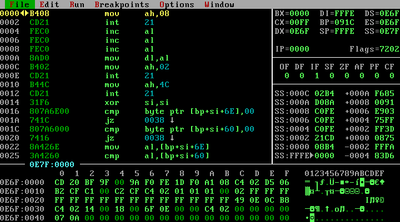
When i load my assembled EXE file in the insight debugger i can see all the correct mnemonic commands in the code window (upper left window), the shown memory address is 0E7F:0000 when the cursor is on the first command which is "mov ah, 08" here. The last command is at 0E7F:0012 and does have the mnemonic "int 21h".
But here's the question, the dump memory window (window at the bottom) is at address 0E6F:0000 and the HEX code shown there doesn't match with the hex code of the code window. See first screenshot for comparsion. (insight.png)
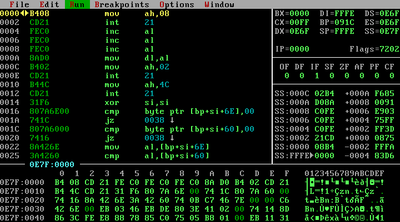
When i do a CTRL+ D search and enter the above address of my code address 0E7F:0000 to go to this address in the "dump memory window", the "dump memory window" shows the correct part of my code. See second screenshot (insight_address_match.png).
Why is this so? Why is the "dumb memory window" showing a completely different memory area/region? Is this a bug of the insight debugger or does this "dump memory window" at the bottom show something other important stuff? If yes, what does it show?
The distance between the Address 0E7F:0000 and 0E6F:0000 is btw. (dec) 274 bytes .